Safeline WAF

A Self Hosted Web Application Firewall
About SafeLine
SafeLine is an advanced Web Application Firewall (WAF) designed to protect web applications from a wide range of cyber threats with robust security measures. Developed by Chaitin Tech, it offers an open-source solution that combines ease of deployment with powerful protection capabilities. Ideal for both enterprise and individual use, SafeLine safeguards applications like the Damn Vulnerable Web Application (DVWA) in this cybersecurity homelab project. It integrates seamlessly with platforms such as Ubuntu Server, providing real-time threat detection and mitigation. This project demonstrates SafeLine's effectiveness in securing web applications against attacks like SQL injection.Key Features of SafeLine:
- Comprehensive Threat Protection: Detects and blocks various attacks, including SQL injection, XSS, and brute force attempts, ensuring robust application security.
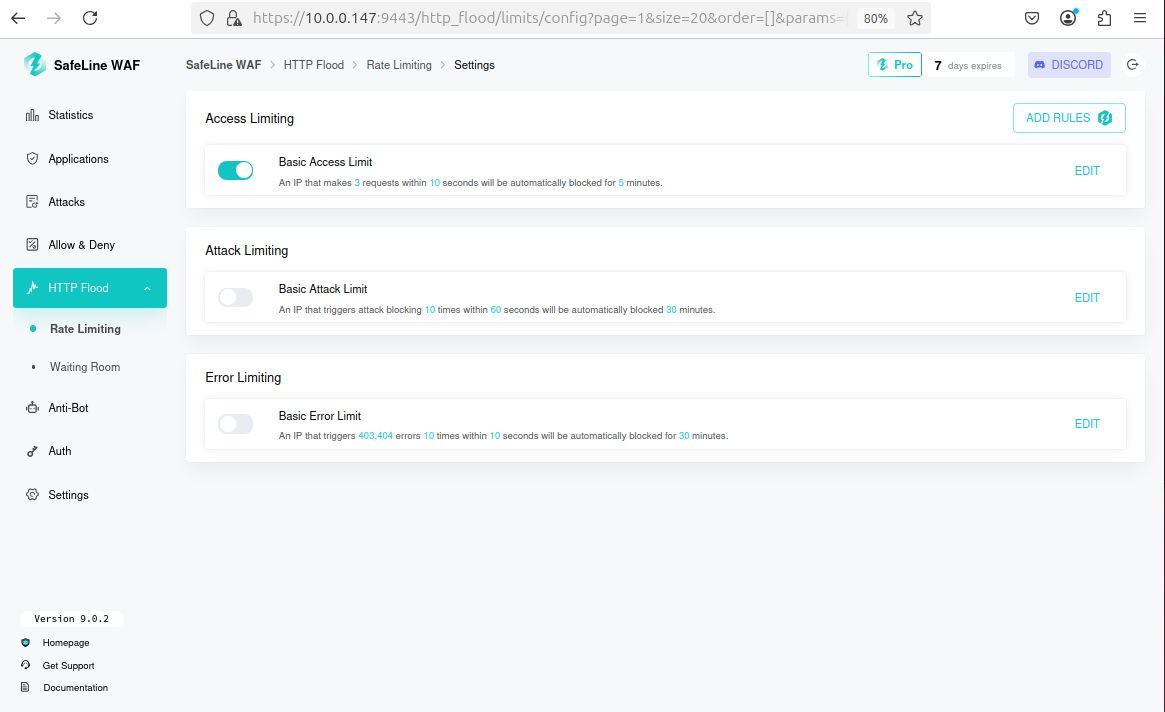
- HTTP Flood Defense: Implements rate-limiting to mitigate denial-of-service (DoS) attacks, protecting server resources from excessive requests.
- Customizable Rules: Allows users to create tailored rules, such as blocking specific IPs (e.g., 10.0.0.41), for precise security control.
- SSL/TLS Support: Supports secure communication by integrating self-signed or custom SSL certificates for encrypted connections.
- User-Friendly Dashboard: Provides an intuitive interface for monitoring traffic, analyzing attack logs, and configuring security settings in real time.
Step 1: Installing Both Machines on VMware
- Kali Linux (IP: 10.0.0.41):
- Download from kali.org.
- Install in VMware with 2 GB RAM, 20 GB disk, and bridged networking.
- Ubuntu Server (IP: 10.0.0.147):
- Download from ubuntu.com.
- Install with 2 GB RAM, 20 GB disk, and bridged networking.
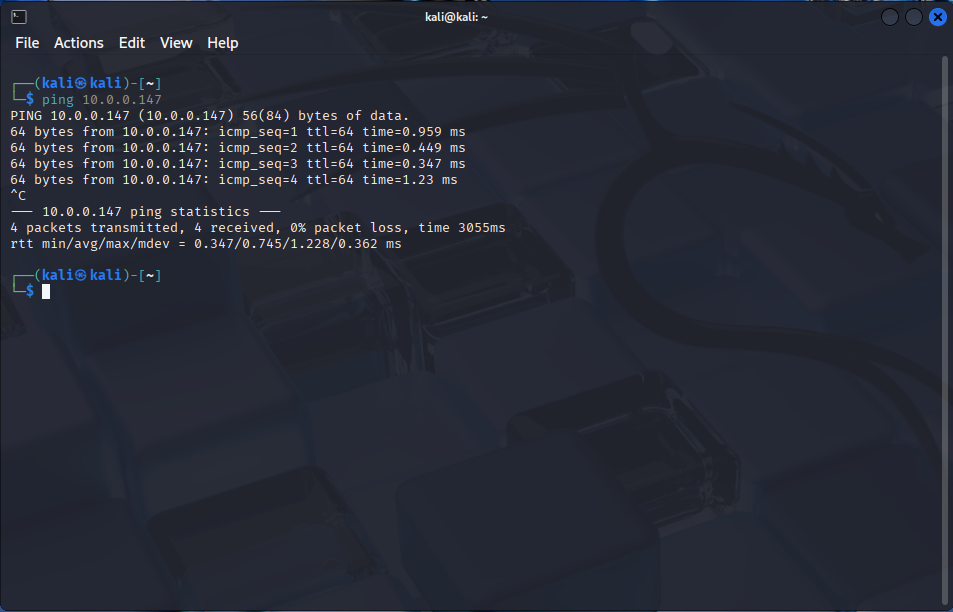
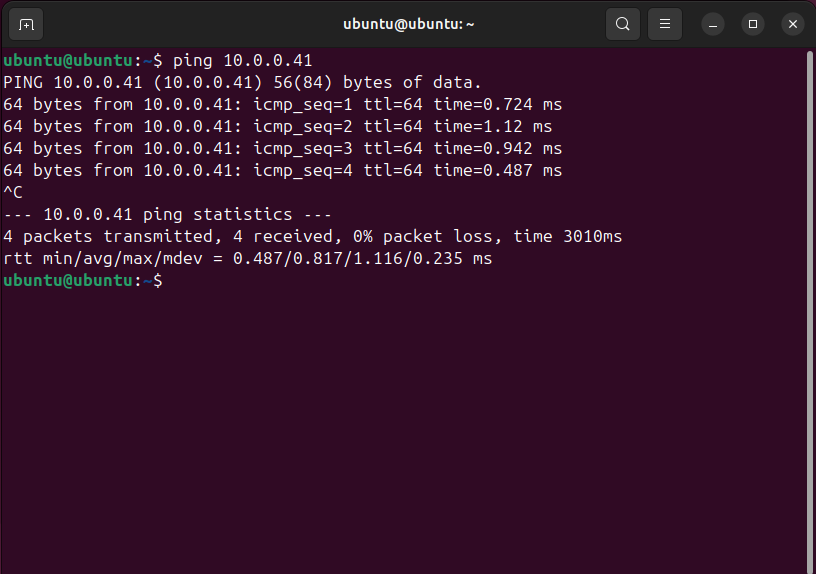
Check IPs and Connectivity:
ping 10.0.0.147 # From Kali
ping 10.0.0.41 # From Ubuntu
Step 2: Prerequisites
2.1 Clone DVWA from git:
cd /var/www/html
sudo git clone https://github.com/digininja/DVWA.git
sudo apt-get install -y git
2.2 Set File Permissions:
sudo chown -R www-data:www-data DVWA
sudo chmod -R 755 DVWA
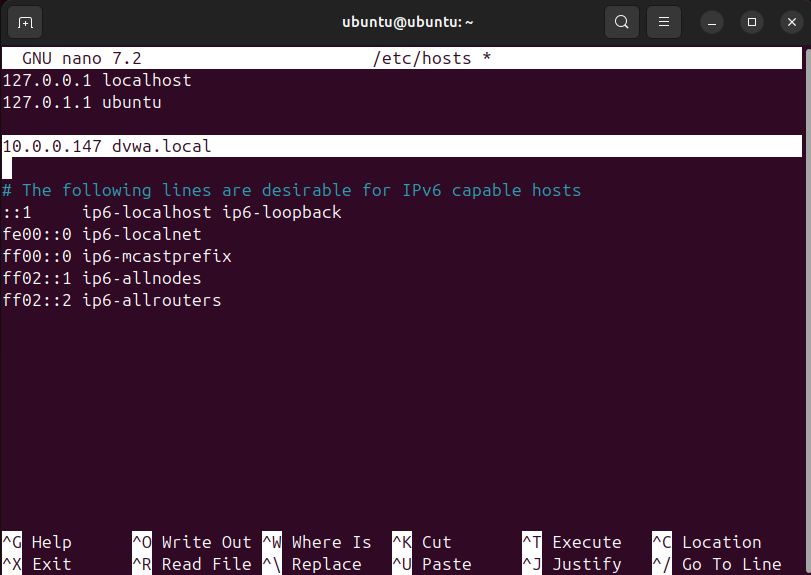
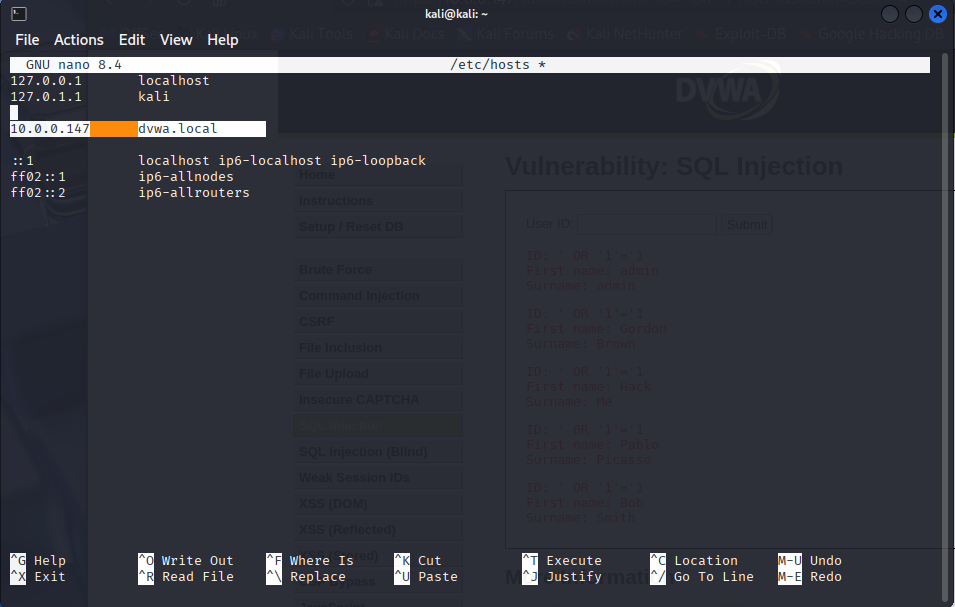
2.3 DNS Resolution Setup
Edit/etc/hosts on both Kali and Ubuntu:
sudo nano /etc/hosts
# Add the following line
10.0.0.147 dvwa.local
2.4 Ubuntu Configurations
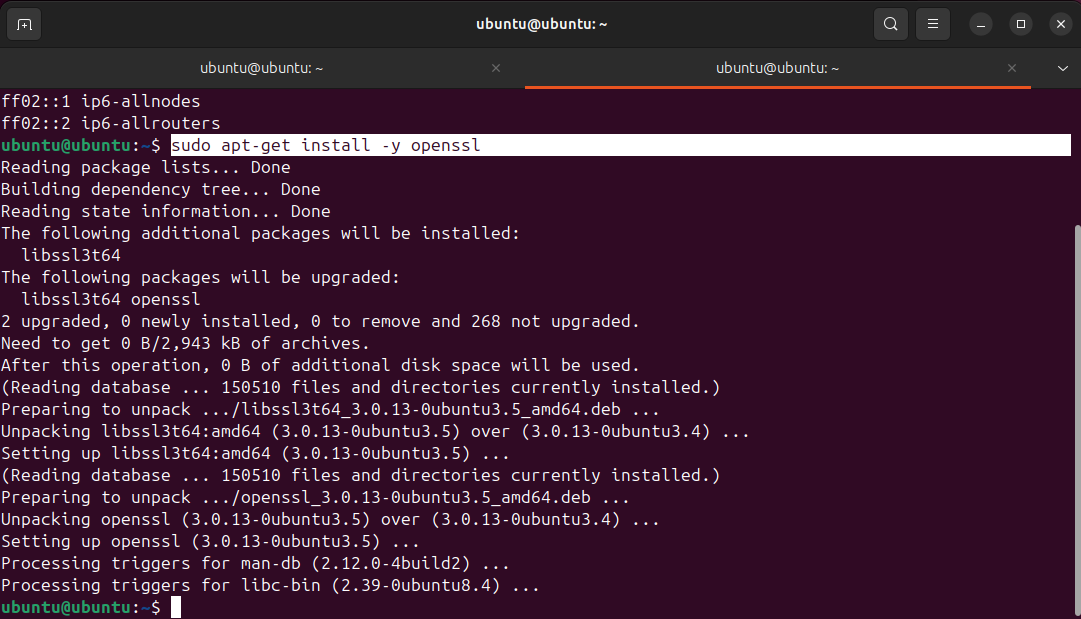
Install OpenSSL:sudo apt-get install -y openssl
Install and Configure LAMP Stack:
sudo apt-get install -y apache2 php php-mysql mysql-server
sudo mysql_secure_installation
# Set MySQL root password: ubuntu (for testing purposes)
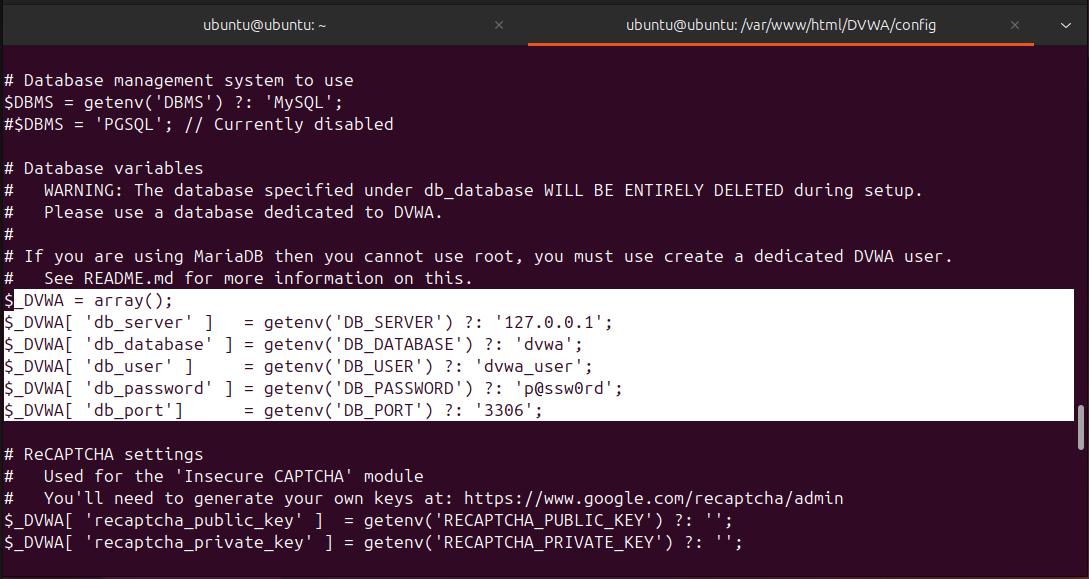
Update DVWA Config File (rename if needed):
// DVWA/config/config.inc.php
$DBMS = 'MySQL';
$db = 'dvwa';
$user = 'dvwa_user';
$pass = 'p@ssw0rd';
$host = 'localhost';
Create DVWA database and user:
sudo mysql -u root -p
CREATE DATABASE dvwa;
CREATE USER 'dvwa_user'@'localhost' IDENTIFIED BY 'p@ssw0rd';
GRANT ALL ON dvwa.* TO 'dvwa_user'@'localhost';
FLUSH PRIVILEGES;
exit;
Navigate to http://dvwa.local/setup.php and click
[Create/ResetDatabase]. 2.5 Change DVWA Listening Port to 8080
sudo nano /etc/apache2/ports.conf
# Change
Listen 80
# to
Listen 8080
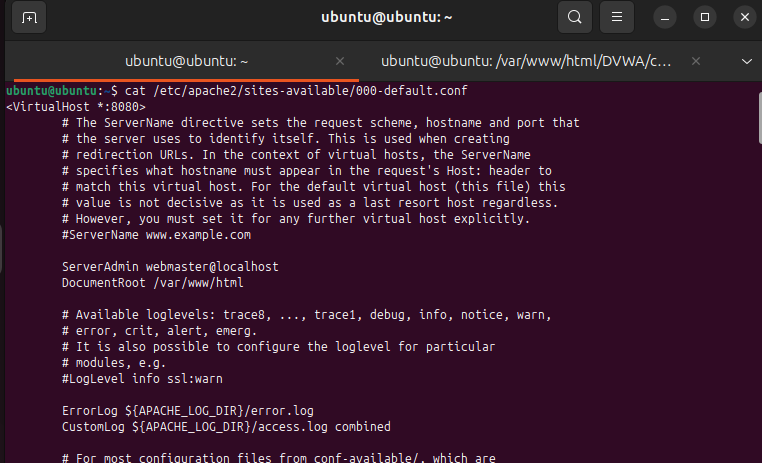
2.6 Change Apache Virtual Host Port
sudo nano /etc/apache2/sites-available/000-default.conf
# Update VirtualHost to
<VirtualHost *:8080>
...
</VirtualHost>
Restart apache
sudo systemctl restart apache2Step 3: Installing SafeLine in Ubuntu
Install SafeLine WAF:bash -c "$(curl -fsSLk https://waf.chaitin.com/release/latest/manager.sh)" -- --en
Reference: SafeLine Official
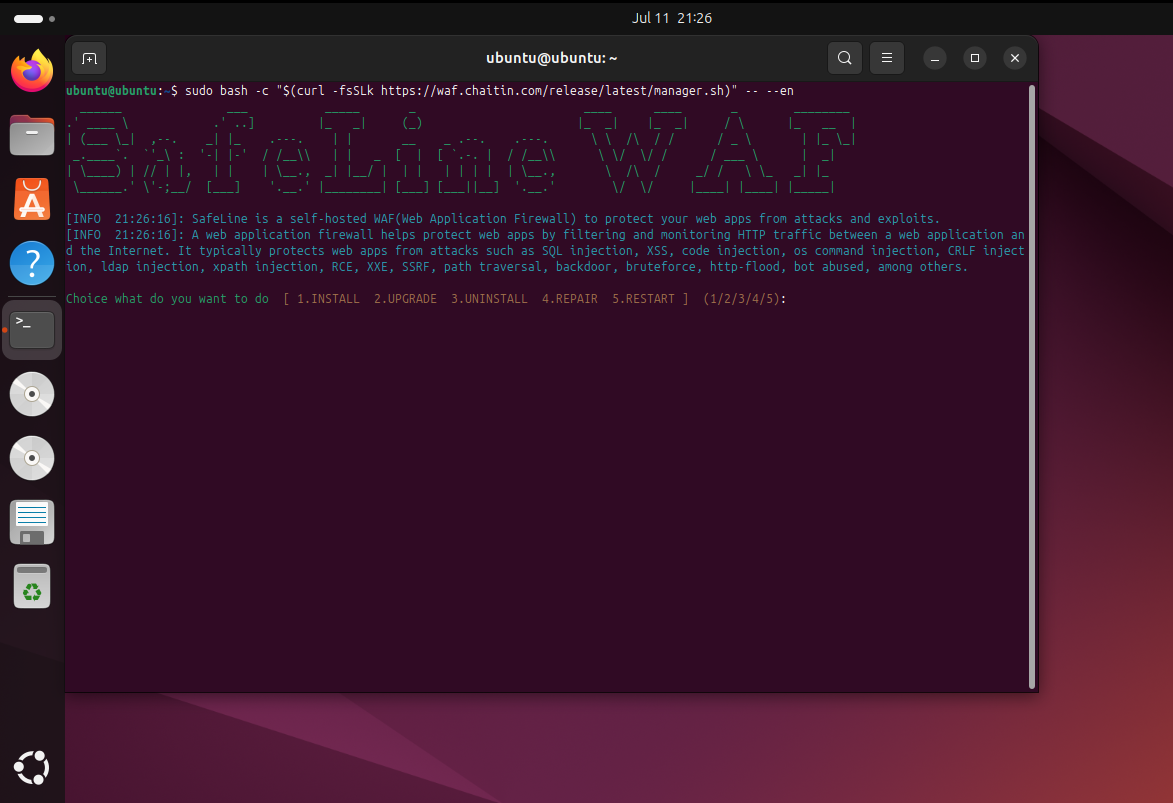 Access the dashboard at https://10.0.0.147:9443 with provided credentials.
Access the dashboard at https://10.0.0.147:9443 with provided credentials.
Step 4: Using SafeLine
4.1 SafeLine WAF Dashboard
- Application Tab: Add DVWA (www.dvwa.local, port 443, reverse proxy to http://10.0.0.147:8080).
- HTTP Flood: Protects against DoS with rate limiting.
- Auth: Provides username/password authentication.
- Used a 7-day PRO license trial.
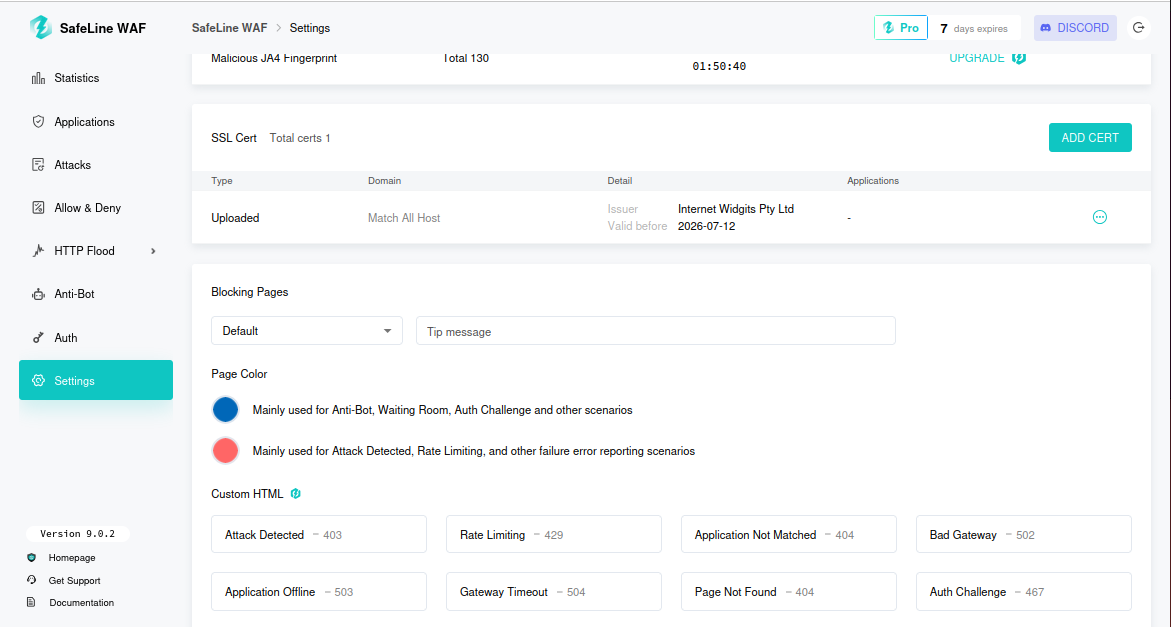
4.3 Creating SSL Certificate
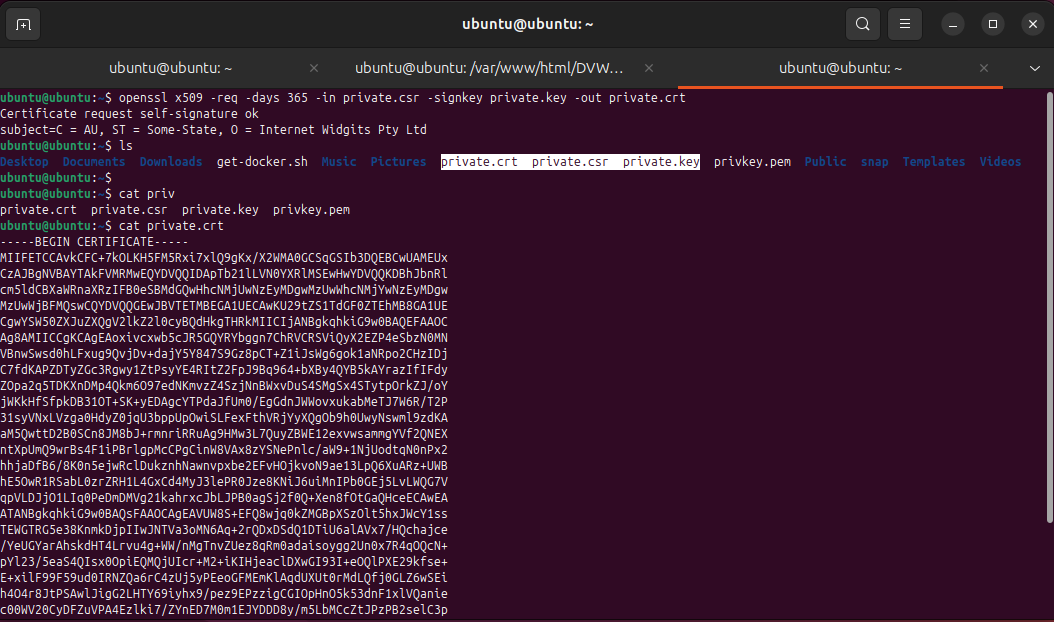
openssl genrsa -out private.key 4096
openssl req -new -key private.key -out private.csr
openssl x509 -req -days 365 -in private.csr -signkey private.key -out private.crt
Import into SafeLine:
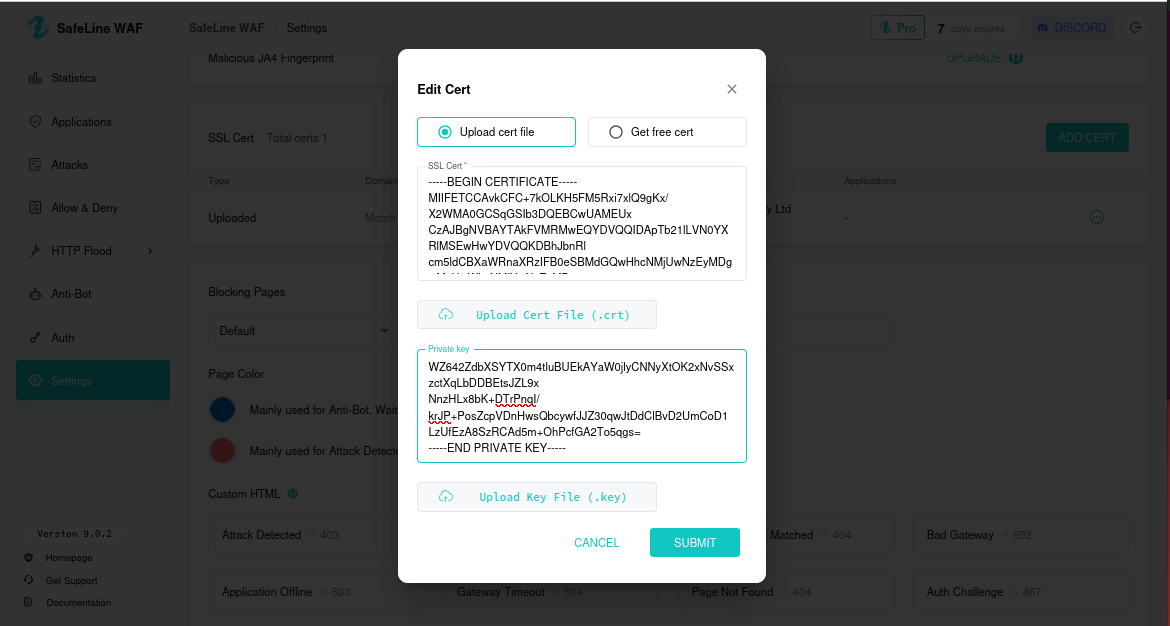
4.4 Testing the Application Rule from Kali Browser
Access http://dvwa.local; it redirects to https://dvwa.local.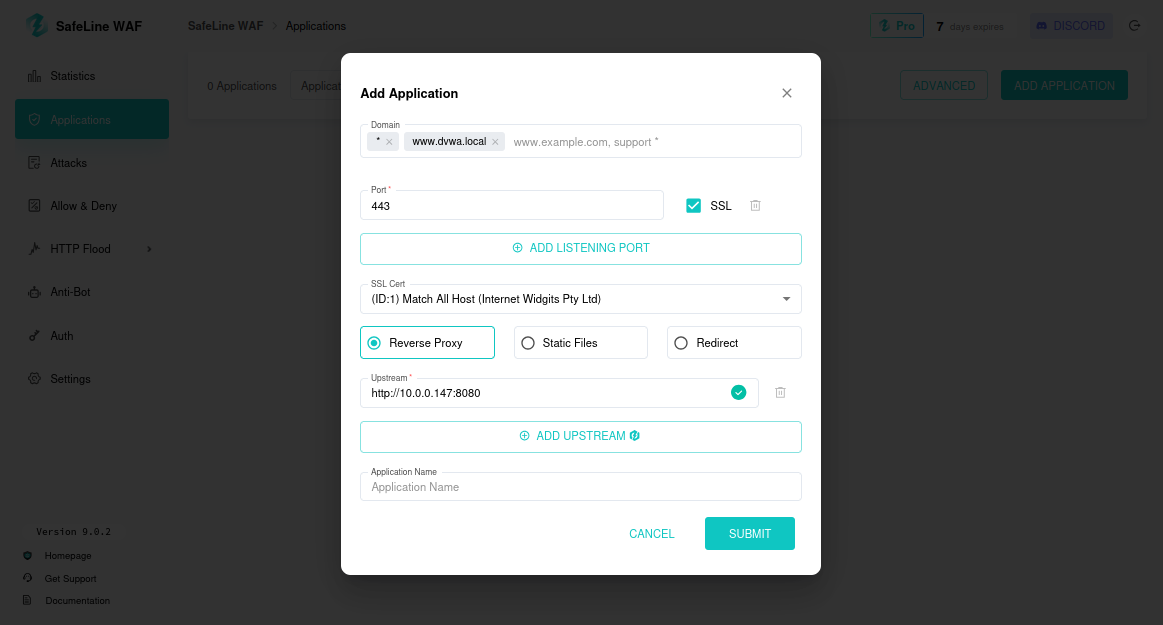
Step 5: Setting up HTTP Flood Rules
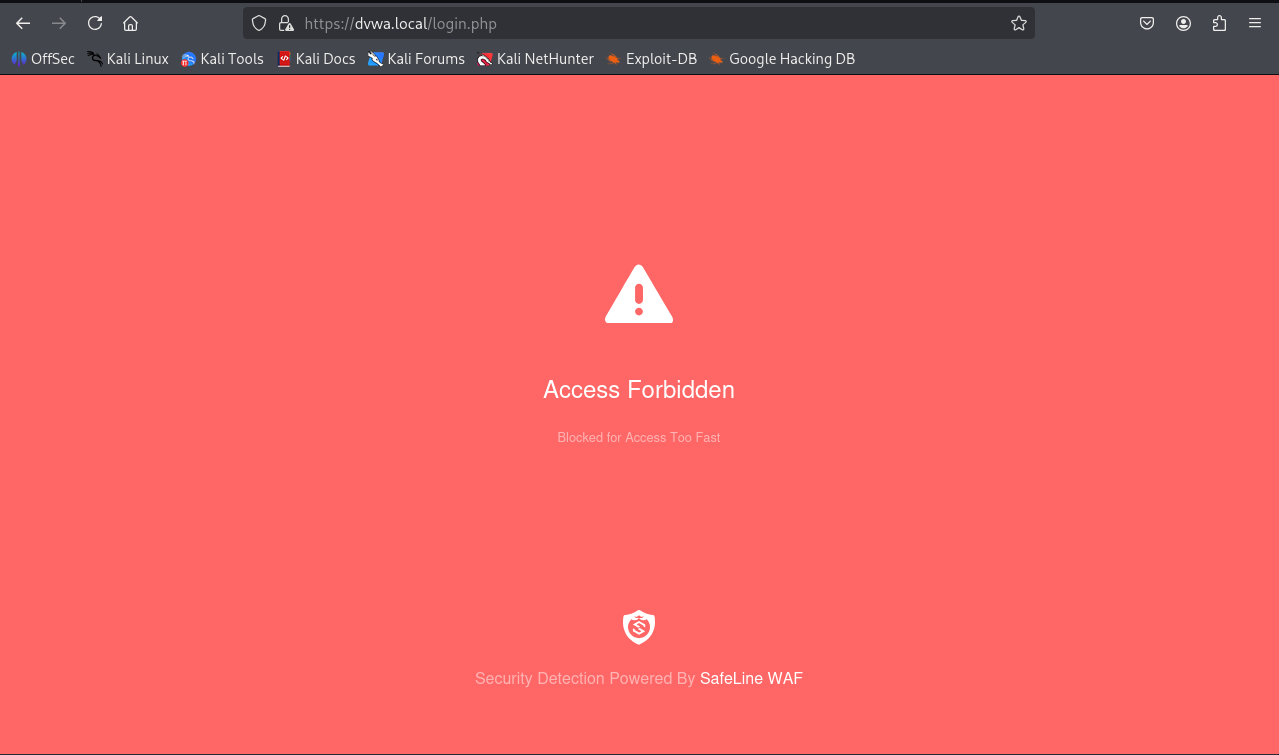
Access is denied if limit exceeded:
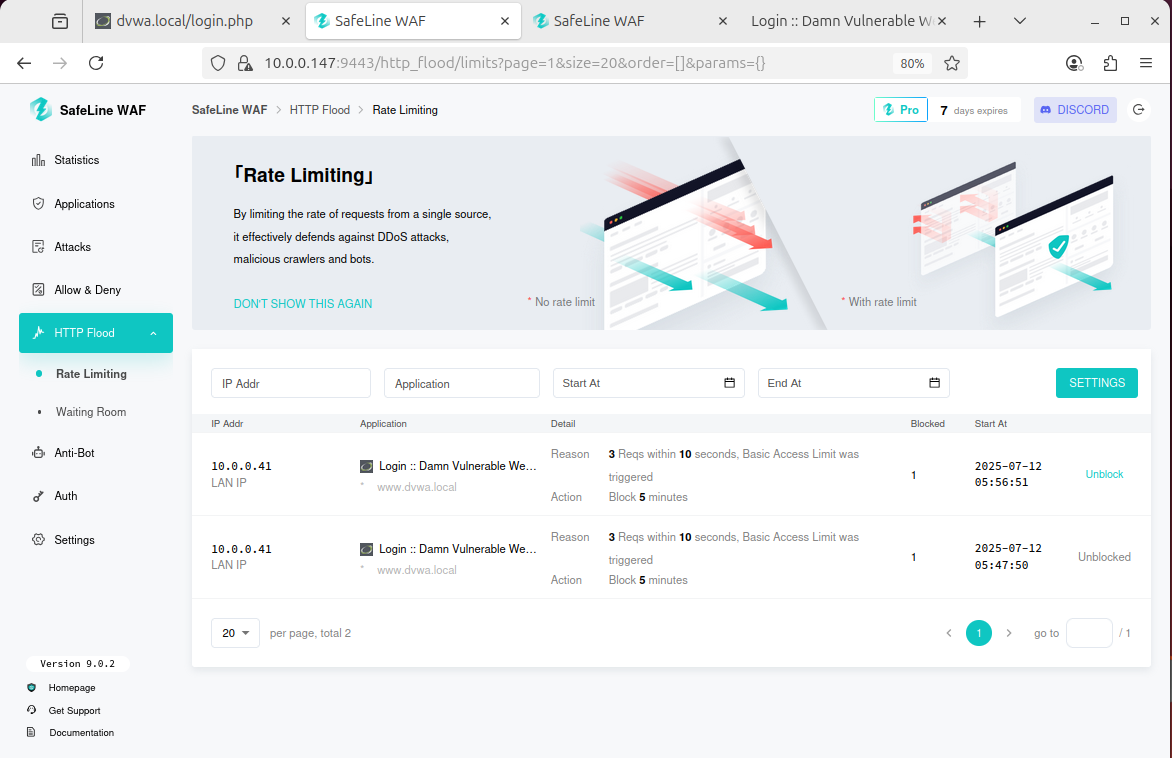
Blocked IPs visible on dashboard with option to unblock:
Step 6: Setting Authentication Rule
Enable authentication in SafeLine with credentials:admin / password
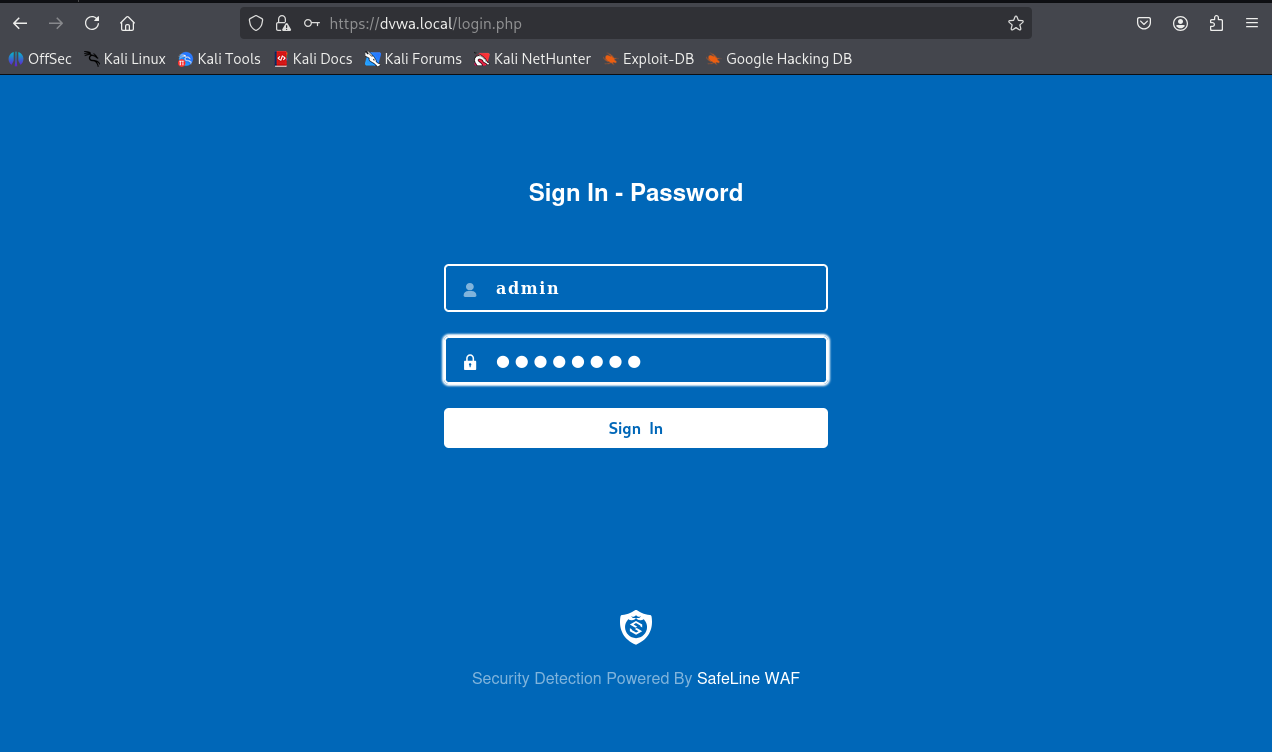
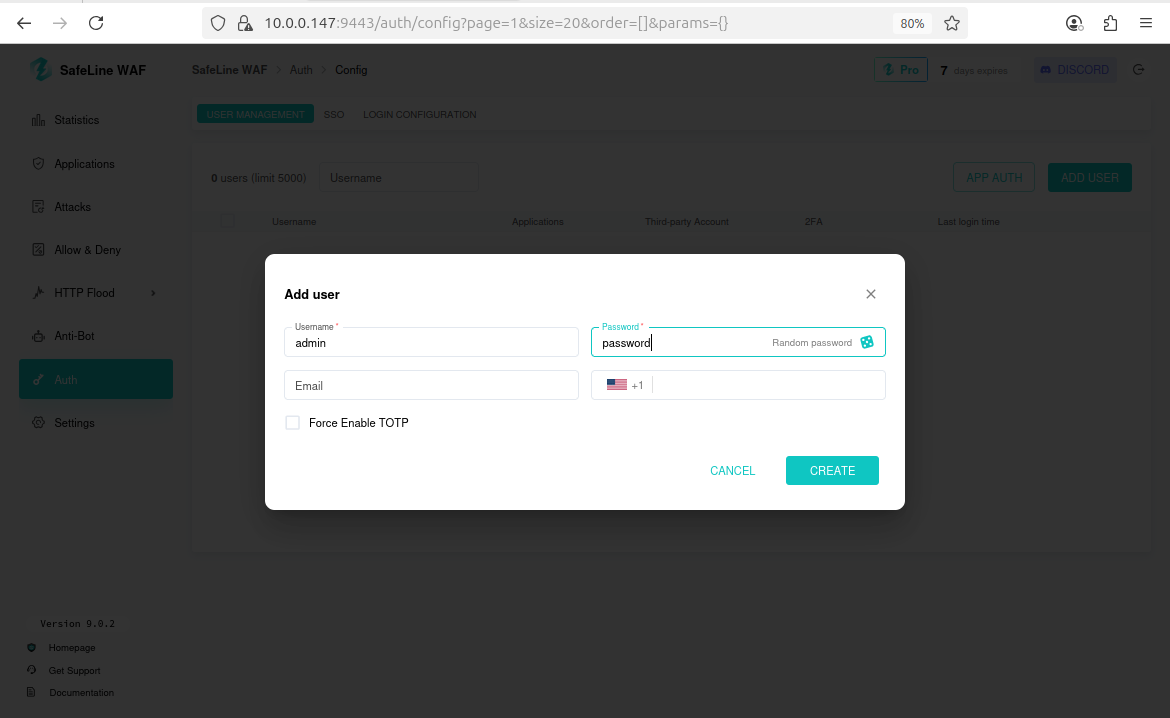 Test from Kali; authentication page appears before DVWA:
Test from Kali; authentication page appears before DVWA:
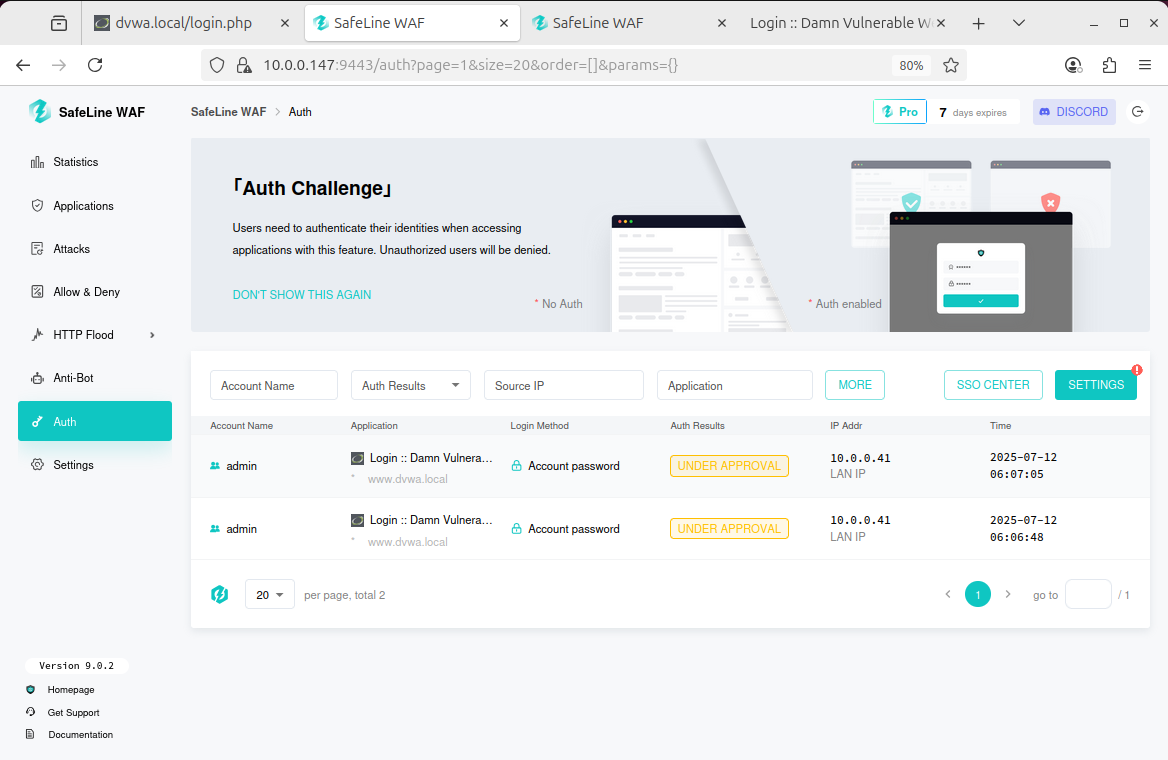
 Firewall captures requests, awaiting approval:
Firewall captures requests, awaiting approval:
Step 7: Creating Custom Rules
Set deny rule for Kali IP (10.0.0.41) in SafeLine: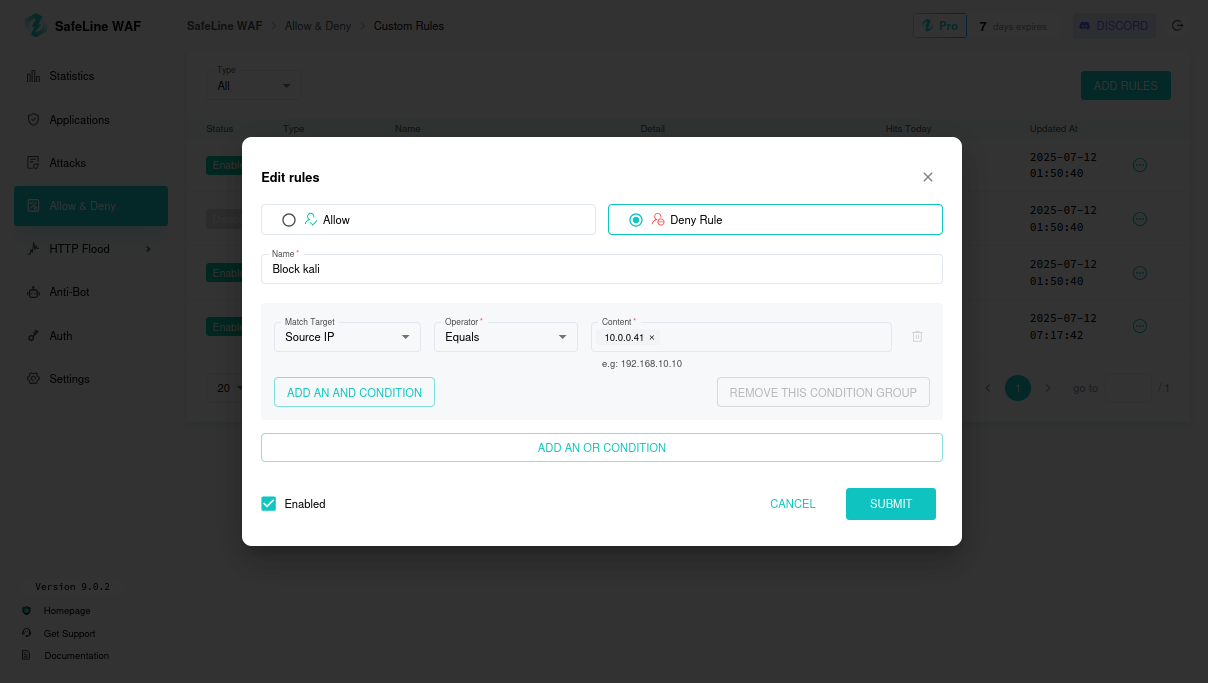 Access blocked from Kali:
Access blocked from Kali:
Step 8: Preventing Attacks
8.1 SQL Injection Testing with Balanced Rules
Set DVWA security to low, try SQL injection (e.g.,admin' OR '1'='1).
SafeLine blocks the attack; check dashboard logs.
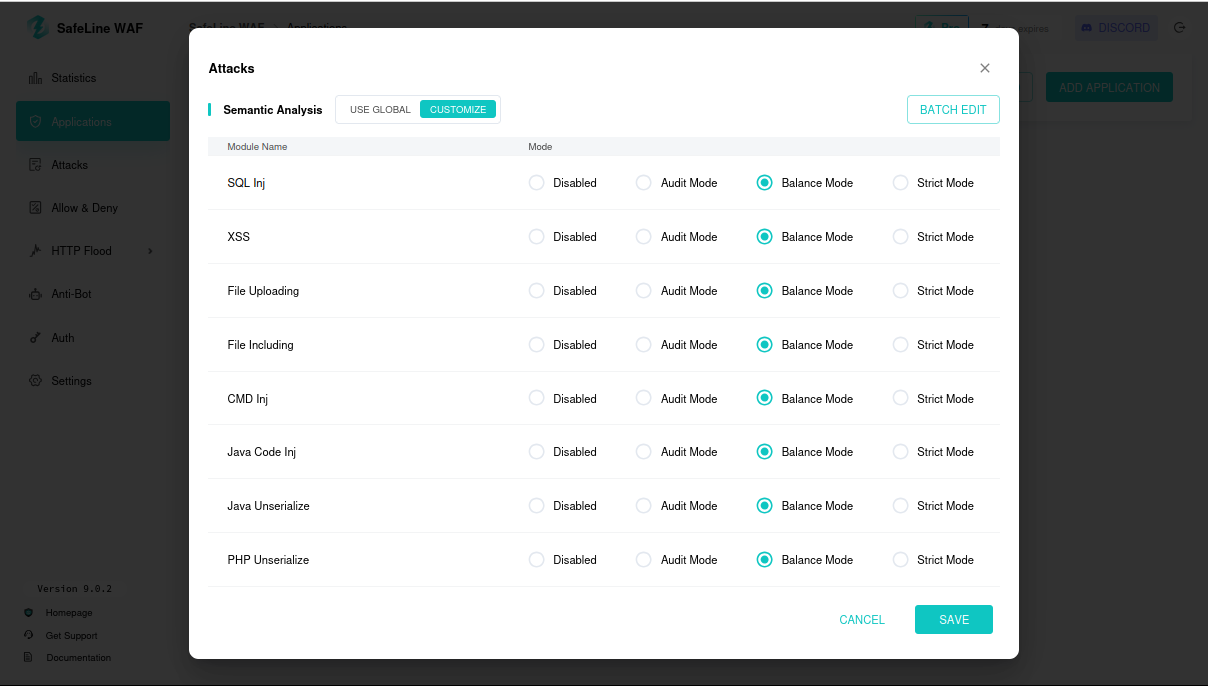
8.2 Disabling Attack Rules
Disable SafeLine attack rules; SQL injection succeeds, exposing usernames/passwords.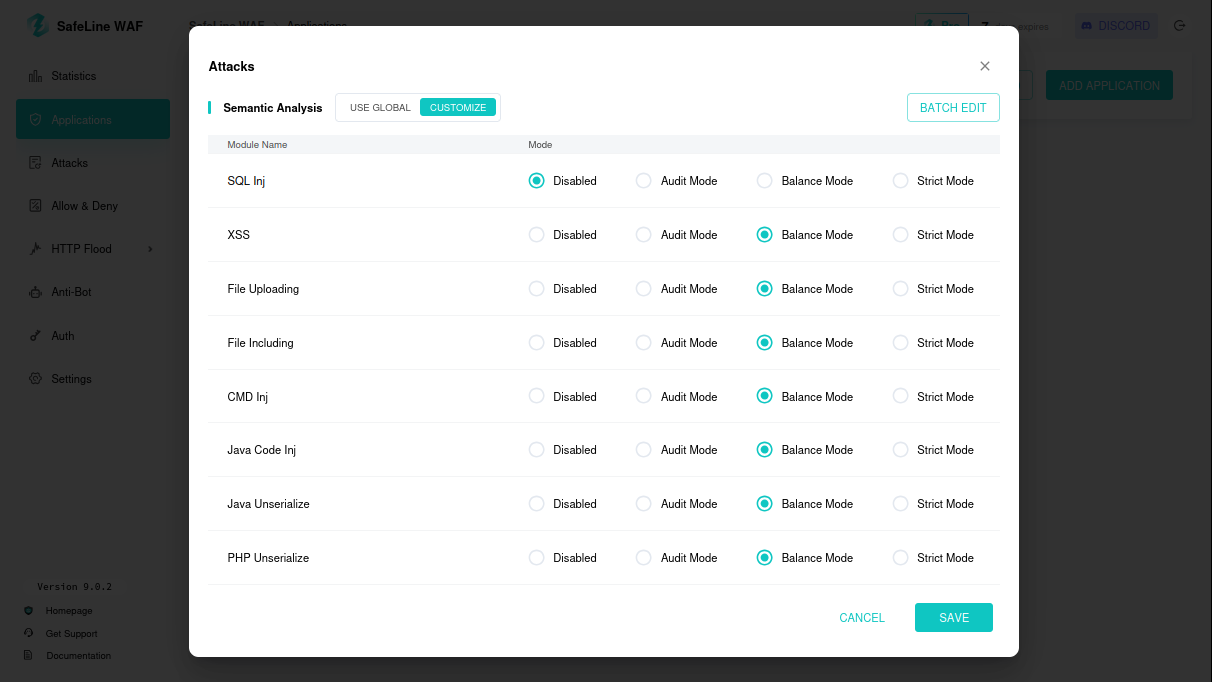
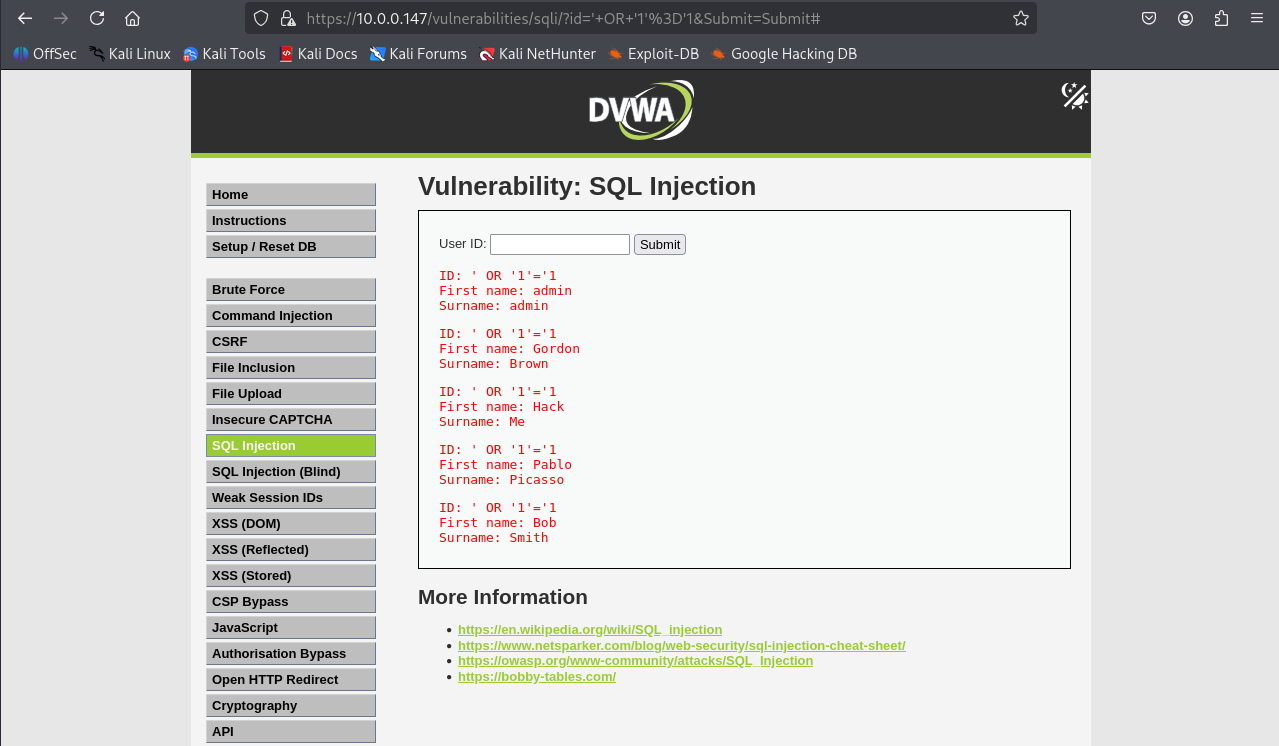
Other attacks like hping, http floods, sqlmap etc. can also be tested and monitored via SafeLine dashboard.
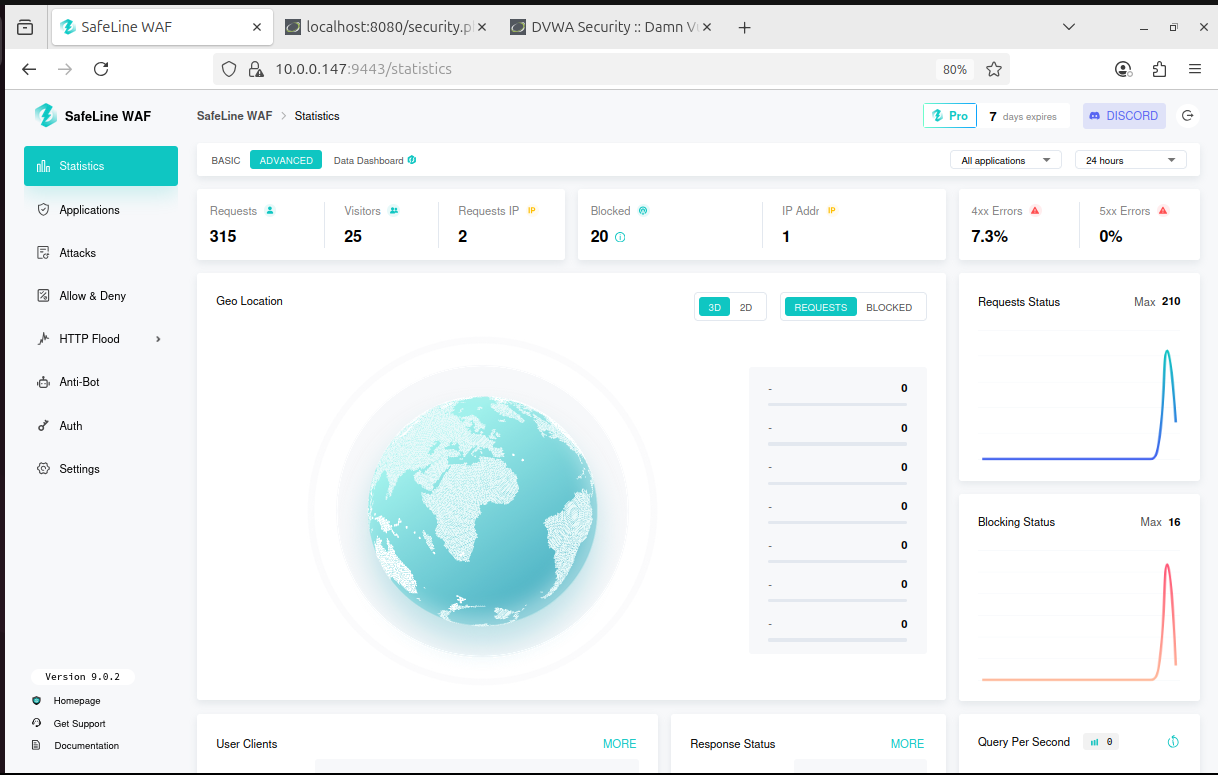
Step 9: Statistics Dashboard
View SafeLine dashboard for request counts, blocked IPs, and attack logs.